With the exponential growth in usage of mobile applications and consumers finding more convenience and ease of usage for different activities, the vulnerabilities associated with mobile apps have also increased. OWASP Mobile Top 10 is one such list that highlights the security flaws & vulnerabilities developers need to protect their applications from.
The list is updated regularly to reflect the changing landscape of mobile security threats. Between 2016 and 2024, there have been significant changes in the types of threats facing mobile applications. These changes may include the emergence of new types of vulnerabilities, shifts in the popularity of certain types of attacks, and advancements in security technology. The OWASP mobile top 10 2024 list guides developers and organizations to stay up to date with these changes in order to protect their mobile applications from potential security breaches.
OWASP Mobile Top 10 2024
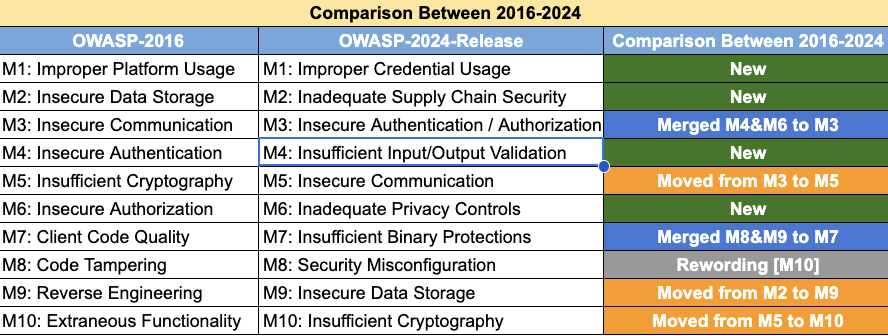
Introducing the OWASP Mobile Top 10 2024 edition – a dynamic reflection of the ever-changing mobile application security landscape. This latest update brings forth a wave of significant changes, encompassing the introduction of fresh categories, the reimagining and refining of existing ones, and the amalgamation of select 2016 categories into more all-encompassing ones.
New Categories in OWASP Mobile Top 10 2024
M4: Insufficient Input/Output Validation:
This new category emphasizes the importance of validating both the input and output data in mobile applications. Proper validation is crucial to prevent issues such as SQL injection, command injection, and cross-site scripting (XSS) attacks. This category highlights the need for rigorous data validation practices to ensure data safety and maintain the integrity of the application.
Example:
A mobile application accepts user input to search for products but does not properly sanitize the input. This allows an attacker to inject SQL commands through the search feature, leading to an SQL injection attack that compromises the database.
Solution:
Implement comprehensive input validation on the client and server sides to ensure only expected and safe data is processed. Use a whitelist approach to accept only known good data. Additionally, output data should be encoded to prevent XSS attacks.
M6: Inadequate Privacy Controls:
Reflecting the growing global concern for user privacy, this category addresses the risks associated with insufficient privacy measures in mobile apps. It focuses on protecting Personally Identifiable Information (PII), ensuring consent mechanisms for data collection, and handling user data responsibly to prevent privacy breaches and legal issues.
Example:
A health tracking app collects and transmits users’ health data without adequately informing the user or obtaining their consent. Additionally, the app fails to provide users with options to control what data is shared, leading to privacy violations.
Solution:
Develop a clear privacy policy that informs users about the data you collect and how it will be used. Implement explicit consent mechanisms before collecting data and provide users with privacy settings to control their data. Regularly review and update privacy practices to comply with legal requirements and best practices.
M8: Security Misconfiguration:
This category deals with vulnerabilities resulting from incorrect or incomplete security configurations. It includes issues such as deploying apps with default settings, misconfigured permissions, and erroneous security settings, which can lead to unauthorized access and data breaches.
Example:
An e-commerce mobile app is deployed with its debug mode enabled, which inadvertently exposes sensitive information through system logs. This includes payment information and personal details that attackers can access if they exploit other vulnerabilities in the app.
Solution:
Regularly audit and review app configurations and deployment environments for security settings. Disable debug information and unnecessary services. Ensure that all system components are set to secure values and that permissions are correctly configured to follow the principle of least privilege.
Categories with Naming and Scoping Changes
M1: Improper Credential Usage (previously Improper Platform Usage):
This updated category highlights the risks associated with the misuse of credentials in mobile applications, such as hardcoding sensitive information or improper management of user credentials.
Example:
A mobile app stores OAuth tokens in plain text within the device’s shared preferences, making it easy for a malicious app installed on the same device to access and use these tokens to impersonate the user.
Solution:
Securely store credentials using the platform’s secure storage solutions, like Android Keystore and iOS Keychain. Avoid storing sensitive information in plain text or in easily accessible locations. Implement additional security measures like encryption and tokenization to protect credentials.
M2: Inadequate Supply Chain Security (previously Insecure Data Storage):
Reflecting the growing importance of supply chain integrity, this category focuses on the risks in the supply chain of mobile apps, including vulnerabilities in third-party components and dependencies.
Example:
A mobile game uses a third-party analytics SDK that contains a known vulnerability allowing an attacker to execute code remotely. The game developers failed to vet the SDK thoroughly, leading to a potential compromise of user data.
Solution:
Conduct thorough security vetting of all third-party components before integrating them into the application. Regularly update these components to incorporate security patches. Use software composition analysis tools to track and monitor third-party dependencies for known vulnerabilities.
M3: Insecure Authentication/Authorization (previously Insecure Communication):
This category now emphasizes the importance of robust authentication and authorization mechanisms in mobile apps to prevent unauthorized access and data breaches.
Example:
A mobile banking app does not require re-authentication for sensitive transactions once a user is logged in. An attacker with temporary access to the device can transfer funds without the device owner’s consent.
Solution:
Implement strong authentication mechanisms, such as multi-factor authentication, to secure user accounts. Ensure that authorization checks are performed server-side for each action that accesses sensitive information or functionality.
M5: Insecure Communication (previously Insecure Authentication):
Renamed to specifically address the risks associated with insecure data transmission, such as the interception of sensitive data due to the use of unencrypted channels or inadequate encryption methods.
Example:
A messaging app sends messages between users without encrypting the data. An attacker on the same network can perform a man-in-the-middle attack to intercept and read the messages.
Solution:
Use Transport Layer Security (TLS) for all data in transit. Implement certificate pinning to prevent man-in-the-middle (MITM) attacks. Ensure that all communication endpoints are secured with up-to-date and strong encryption algorithms.
Consolidated Categories
M7: Insufficient Binary Protections:
This category combines the risks associated with code tampering and reverse engineering from the 2016 list. It focuses on protecting the binary code of mobile apps from being tampered with or reverse-engineered.
Example:
An attacker uses a tool to reverse engineer a popular mobile game’s binary to find and exploit a vulnerability that allows them to unlock premium features without payment.
Solution:
Use obfuscation techniques to make reverse engineering more difficult. Implement tamper detection mechanisms that alert you or invalidate the app if modifications are detected. Use tools that harden the binary against attacks.
M9: Insecure Data Storage:
Now includes the risks related to extraneous functionality from the 2016 list. It emphasizes the need for secure storage practices and strong encryption to protect sensitive data stored on mobile devices.
Example:
A fitness app stores workout history and location data in an unencrypted database file on the device. If the device is lost or stolen, an unauthorized individual could access this sensitive information.
Solution:
Encrypt sensitive data stored locally on the device using strong encryption algorithms. Ensure that encryption keys are securely managed and not hard-coded into the application. Apply secure storage practices provided by the mobile operating system.
M10: Insufficient Cryptography:
Combines the risks associated with broken cryptography from the 2016 list. This category highlights the importance of using strong and properly implemented cryptographic practices to ensure data confidentiality and integrity.
Removed Category
M7: Client Code Quality:
This category from the 2016 list has been merged with M4 (Insufficient Input/Output Validation) in the 2024 edition.
The OWASP Mobile Top 10 updates released recently highlight the ever-evolving landscape of mobile security threats and the industry’s proactive measures to combat them. The OWASP Mobile Top 10 2024 offers a comprehensive framework that equips developers, testers, and security professionals with the knowledge and tools to effectively tackle the most pressing security risks in mobile applications. To delve deeper into each category and access detailed information and prevention strategies, AppSealing is right there for your assistance.





